The past couple of months, with Nicolas and Louisiane from Eurazeo, we explored the broader “Identity Software” space with great interest. The way people and businesses manage their online identity is currently evolving fast and we wanted to have a better overview of the exciting trends shaping this space.
This post summarises our main findings regarding the B2B side and we’ll update it with consumer related trends in the next months. If you want to get in touch, don’t hesitate to contact me clement.vouillon@gmail.com.
Table of content:
- If you have 5 minutes:
- If you have 30 minutes:
- If you have 1 hour:
- List of the companies on the map
- Startups unpacking
TL;DR:
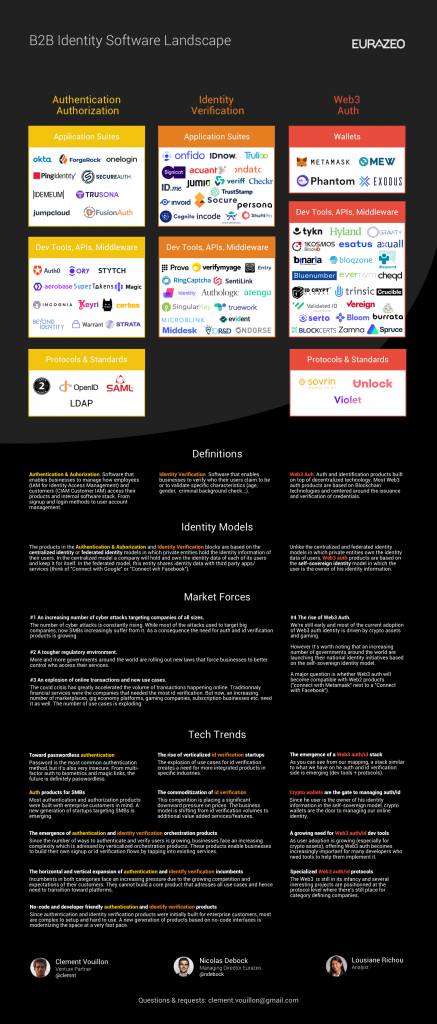
If you only have 5 minutes available, just check our cheat sheet (click on the pic to download the full size file):
Videos
The videos cover in greater details the findings of our deep dive into the B2B Identity Software space (around 30min in total).
1- Introduction to our deep dive
What is the scope of our deep dive?
The notion of “identity” is very broad and encompasses many different aspects from very technical to more philosophical ones.
We don’t pretend that we can cover all of it. It’s an impossible task that we cannot achieve. Our goal is much more modest and is simply to share a 10 000 feet overview of the Online Identity Software space.
By Online Identity software we mean all the products that are used to identify, authenticate and authorize people and businesses to access services or conduct online transactions. Whether it’s for employees to access the internal tools of their company, or an individual who needs to prove his identity. This Includes the end user applications but also the infrastructure used to build them.
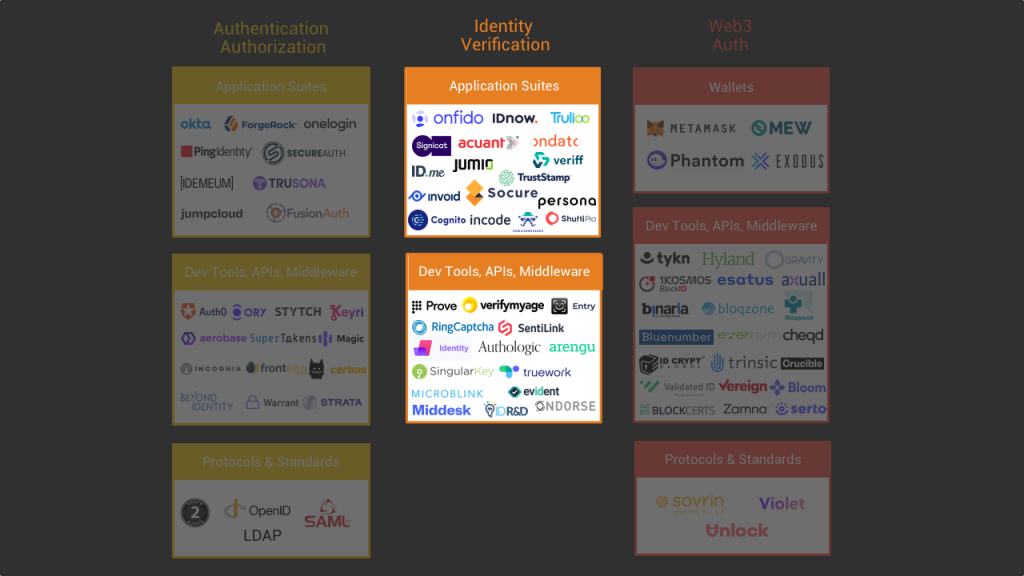
Our Mapping
A big part of our deep dive was to see whether we could create a comprehensive mapping of this space. We ended up decomposing the broader online identity software space into three major blocks covering the whole B2B spectrum.
First, on the B2B side we have the authentication and authorization block which include the products that enable a company to create and manage everything around how employees and customers access applications securely. From single sign on systems for employees to active directory management or customer account management. It’s the territory of multi-billion dollar companies such as Okta or OneLogin..
The second major block is the identity verification block. It’s the other side of the B2B identity software coin. If with the authentication and authorization block a business has all the tools it needs to log in and out users, there are also many cases where they need to verify the identity of a person before it creates an account or before it initiates a transaction.
Historically identity verification services such as Onfido were mostly used by financial services businesses, but as we’ll see it briefly, the need to verify user identity is exploding and is becoming a requirement in many industries.
The next block on our map is the Web3 auth block. What is interesting here is that many crypto identity projects are at the intersection of B2B and B2C. As we’ll see, there is a growing number of identity services based on blockchain technologies that are changing how user authorization/authentication and identity verification are made. This whole Web3 auth trend is super exciting and could have a big impact on the future of this space.
2- User Authorization and Authentication
What is user authorization & authentication software?
As I briefly explained previously, the authorization and authentication block groups the software and tech that enable businesses to login and manage securely the accounts of their employees or customers. We divided this category into a stack of three layers.
- At the bottom we have the major protocols and standards on which most applications are built. For example Oauth2 is one of the most used standards for authorization and OpenID for authentication.
- On top of the stack we find the applications that are in general turnkey solutions that businesses use out of the box such as Okta.
- In the middle we have all the APIs, middleware and developer tools which enables developers to build their own auth product or process.
Market forces: What is happening in the auth space?
#1 An increasing number of cyber attacks impacting companies of all sizes
One of the reasons why user authorization and authentication software is so crucial is obviously because of security. A company cannot let unauthorised users or hackers access their internal tools or products.
And this is also why this market is growing at the moment since there’s an increasing number of cybersecurity attacks against businesses of all sizes. The need to secure and manage user identities is of growing importance for companies.
#2 People use more and more online products
Another factor is the ever increasing number of online products on which you need to authenticate. Social media, ecommerce, business applications, mobile apps (etc. etc.), the average person needs to login to more and more products. Just to give you an order of magnitude, AWS identity shared that their API handles 400M API authentication and authorization calls every second. 400M every single second.
#3 A never ending race between attackers and auth providers
The third aspect to keep in mind is that hackers are constantly trying to find new ways to sneak in and as a consequence there’s a never ending race between the auth service providers and the hackers that require these products to evolve constantly. This is why we went from simple password to multi-factor authentication and now even biometrics authentication methods.
#4 An more and more complex regulatory environment
Last but not least, businesses face an increasing pressure on the regulation side as stricter legal requirements are rolled out regularly in most countries. Businesses cannot take user authentication and authorization lightly anymore.
What products did we put in the authentication and authorization blocks of our mapping?
Now let’s briefly go over each layer of our authorization and authentication block starting with the protocols and standards layer.

Here you’ll find all the protocols and standards, such as OAuth 2, that are generally used to build authorization and authentication products. Many of them are open source projects created and maintained by communities of developers. I will not dig more into this layer as I am not knowledgeable enough about it and as it does not bring much for the purpose of our deep dive.
The application layer is probably the one that most people are familiar with. In it you’ll find the companies that offer ready to use auth products that enable business to sign in, authorize and manage users out of the box. If you’re a business and don’t want to code yourself the infrastructure to let your employees and customers sign up with their email for example, you will adopt such solutions. It’s worth noting that all the bigger players such as Okta or OneLogin bundle together the authentication and authorization features, but specialized products do exist.
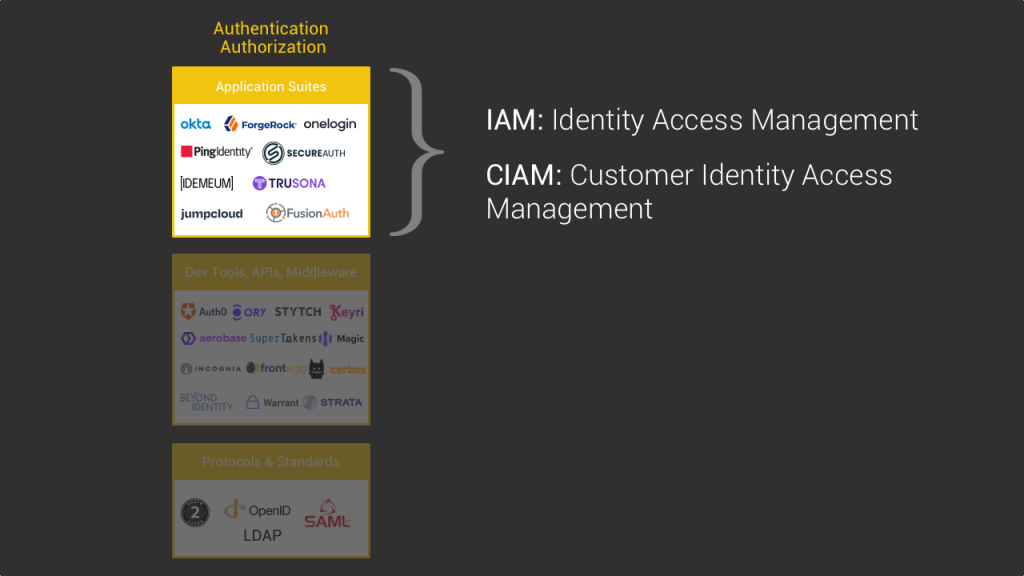
Another important aspect to keep in mind is that we can differentiate two types of auth products: the ones specialized in employee account management (also called IAM for identity Access management) and the ones dedicated to managing your customers accounts which is called CIAM for customer identity management. The biggest players in the field such as Okta offer both IAM and CIAM but you’ll also find specialized players as managing employee and customer accounts require different features.
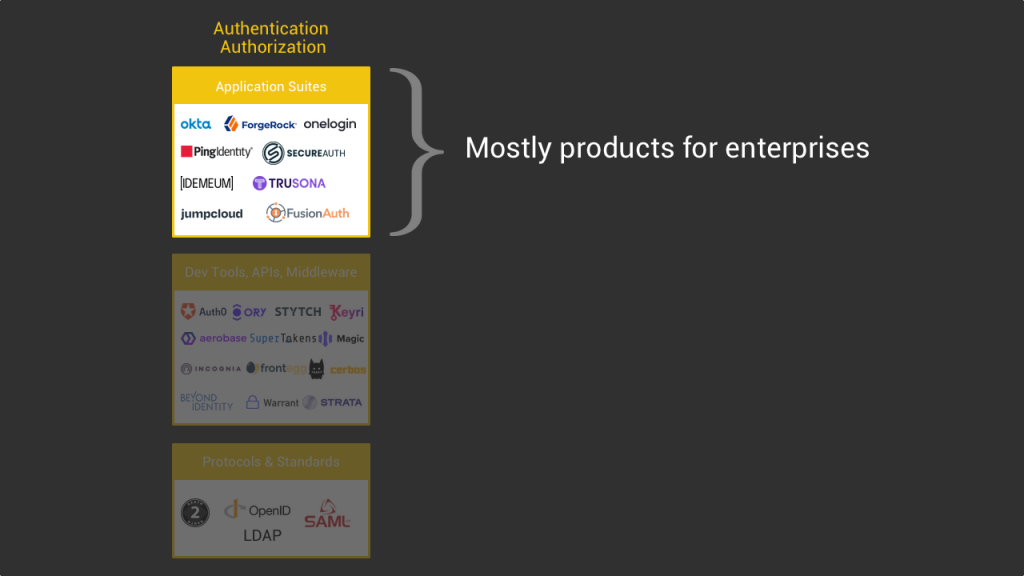
What is interesting to notice here is that most of the products in that layer are made for enterprise customers. Large companies have a real need and also the resources to put in place a solid auth infrastructure. It’s a key security element that they cannot play with if they don’t want to be hacked or face legal troubles. This is why they’ll spend millions of dollars on auth software. It’s definitely a must-have type of product for them.
On the other hand, small businesses do not have the resources to put in place customized auth infrastructure. This is why whether it’s for their employees or customers, they will not own the auth infrastructure but rather use the one provided by the major platforms. For example many small businesses will rely on the Google suite to provide single sign-on to their employees and manage their email as well as access other internal software. When it comes to CIAM it depends on the type of industry the small business is, but for example an ecommerce company that uses Shopify will use Shopify’s baked-in customer access management and not recreate its own.
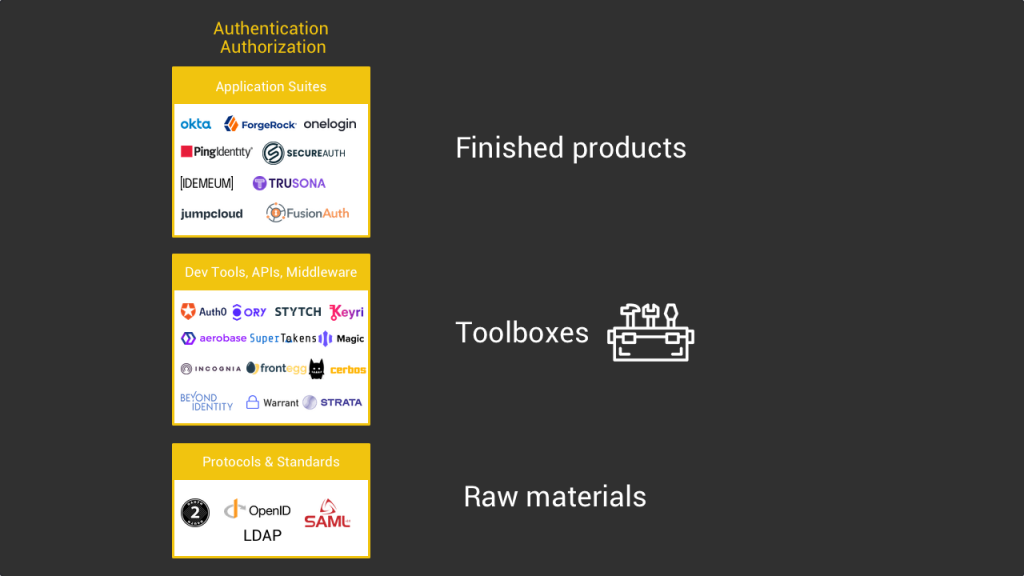
Now let’s move on to the API/middleware/developer tools layer of our stack. The difference between the application and the developer tools layer is that in the application layer you have mostly turnkey solutions which are ready to use by businesses, whereas in the middleware layer you have the products that enable developers to build their own user authentication/authorization process.

To use an analogy it’s like if in the protocol layer you have all the raw materials required to build a user auth system. In the application layer you have the finished products that you can use directly without having to build it yourself. And in the middleware layer you have toolboxes that help developers build their own auth products. A good example of such a toolbox is Ory which enables developers to build their own CIAM based on existing open source protocols such as 0auth2.
Tech Trends
Now that I have explained a little bit more the differences between each layer, let’s go to the real meat of this deep dive and explore the trends that are currently shaping this authentication and authorization identity block.
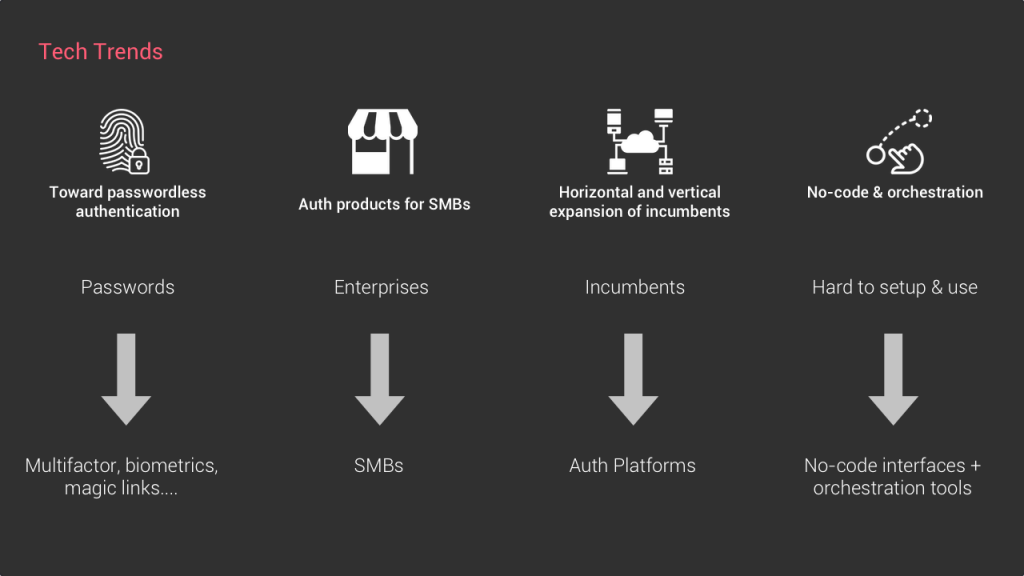
#1 Toward passwordless authentication
One of the first obvious trends happening is the evolution of how users actually sign up and login. In many cases, users access their account thanks to a password. But the issue with this method is that passwords are quite insecure. Whether it’s because users create very weak passwords or always use the same one or because hackers regularly collect huge amounts of passwords, it’s definitely not bulletproof.
As I said earlier, auth products must constantly evolve because there’s an ever ending race with hackers. This is why the past couple of years we saw the rise of multi-factor authentication for example. Or biometric authentication based on fingerprint or even face recognition. The trend is definitely going toward passwordless authentication, and a growing number of startups like Keyri or Magic are building such solutions.
#2 Authentication solutions for SMBs
As I mentioned in the intro, traditionally standalone authentication solutions such as Okta or OnelLogin target the enterprise segment and the SMBs tend to use the authentication infrastructure of existing platforms such as Google. But since cybersecurity attacks now impact even small businesses, there’s a growing need for the “okta of Small businesses”. A new breed of startups such as Idemeum, which provides a single place for small businesses to setup and manage employe access to SaaS, is emerging
#3 The horizontal and vertical expansion of incumbents
If you take into consideration the two trends I’ve just covered, you understand quickly that there’s a lot of pressure on the incumbents such as Okta to expand their product both horizontally and vertically if they don’t want to become irrelevant.
They increasingly need to appeal to users that go beyond the pure Enterprise software. It’s the reason why, for example, Okta acquired Auth0, a developer tool. Or that they start to go down-market with products accessible to small businesses. For sure we’ll see more acquisitions happening in this space in the next months.
#4 The emergence of orchestration and no-code middleware services
When we looked at what is happening in the API/middleware/developer tools layer, two trends stood out: no-code and orchestration tools. Since there’s an increasing number of ways to authenticate users, businesses need to navigate through this increasing complexity more easily. Orchestration products, such as Arengu, enables companies to build their own signup and signin flow by tapping into existing services simply through a drag and drop interface.
It is worth noting that the incumbent of the auth space also move toward the role of auth platforms and want to offer orchestration features to their customers for more flexibility.
#5 The rise of web3 auth?
The last trend that I will just evoke here is the potentially coming age of what is called web3 auth. We’ll cover it in more detail in the video dedicated to the crypto block, but many people believe that we’re on a path of having completely new ways to authorize and authenticate users thanks to blockchain technology.
3- Identity Verification
What is identity verification software?
The identity verification block is the other side of the B2B identity software coin. If the products in the authentication block are about how to let users login and after how to manage their account, the products in the verification block enable businesses to verify and validate the identity of their users when they register or conduct a transaction.
And similarly to what we did for the authentication block, we divided the identity verification block into a stack of two layers.
- In the application layer you’ll find the products that enable businesses to verify the identity of their users “out of the box”, often with turnkey solutions. Some well known companies in this layer are Onfido or Idnow.
- Then you have the API/middleware/dev tools layer which groups all the tools that enable developers to create their own id verification process or the tools which are specialized on specific tasks, such as analyzing identity document scans for example.
Market forces: What is happening in the id verification space?
What was super interesting to see when we explored this space is how fast this market is currently changing and growing. The need for identity verification is literally exploding.
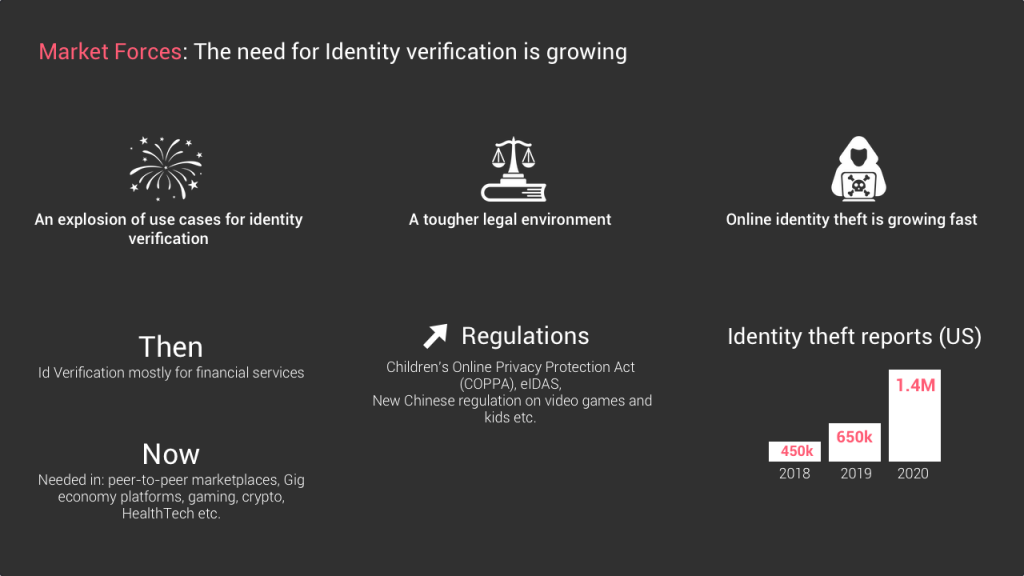
#1 An explosion of online transactions for an increasing number of use cases
The first obvious reason is the explosion of online transactions that require an identity verification. The covid crisis has greatly accelerated the volume of transactions happening online, and an increasing number of them require a minimum of identification verification.
Historically, many of the identity verification providers were built for financial services, Whether it’s a bank or other payment providers, the majority of financial services require an id proof before you can conduct a financial transaction in order to avoid theft and other money laundering problems.
But what is happening is that this need is now felt in many more categories that go beyond financial services. For example, more and more gaming companies need to control who accesses their services, same with peer-to-peer marketplaces, Gig economy platforms, social media apps, many crypto platforms as well, health product providers, consumer subscription businesses etc. etc.
#2 A tougher regulatory environment
This explosion in terms of use cases is followed by an increasing pressure from the legal side. Many governments are rolling out new legislation that forces businesses to have more control over who accesses their service. For example social media platforms such as instagram are legally forced to restrict the access of users below 13 years old. Obviously many will lie about their age, this is why solutions based on pattern usage recognition are used for example.
As a telling sign of the growing importance of online identity “The European Commission proposed a framework for a European Digital Identity which will be available to all EU citizens, residents, and businesses in the EU. Citizens will be able to prove their identity and share electronic documents from their European Digital Identity wallets with the click of a button on their phone” (source)
#4 An ever ending race with hackers that require increasingly complex verification processes
Finally, similar to what is happening in the authentication space, hackers and other bad intended entities are coming with increasingly sophisticated attacks to steal and fake identities. So the verification providers are in an ever ending race to improve their product to answer these new threats.
So you understand why for all these reasons the identity space is currently fast changing and a lot of exciting trends are accelerating.
What products did we put in the identity verification category of our mapping?
Now let’s briefly cover the two layers of our id verification stack starting with the application one.

In this layer you’ll find the products that enable businesses to directly verify the identity of their users “out of the box”.
Identifying and verifying users is actually a very complex process that can take many forms depending on the particular use case. I think that most of you have already uploaded a photo of your identity card in order to use an online banking app or to initiate a money transfer. If it’s probably the first thing that comes to mind when we think of id verification, what is interesting to notice is that the ways to identify users keep growing.
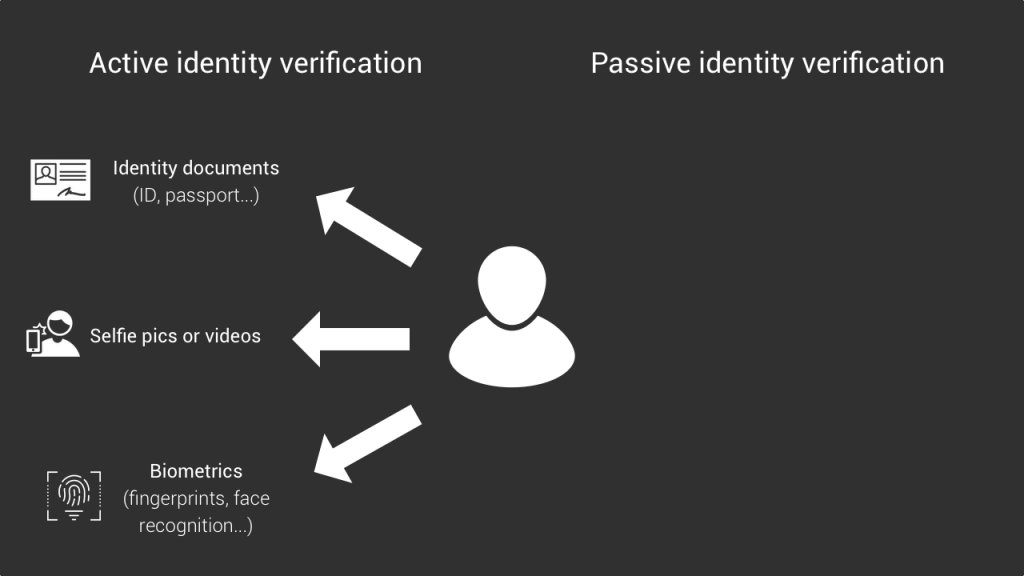
First, when it comes to actively verifying your identity, you can obviously use government issued documents. But other types of documents are now used such as uploading a selfie, recording and uploading a video of yourself or even using biometrics to confirm who you are. The way to actively confirm your identity keeps growing and, in the background, companies need to build products that are increasingly sophisticated, with AI for example. However it’s worth noting that almost most of the time human intervention is still required in these companies.
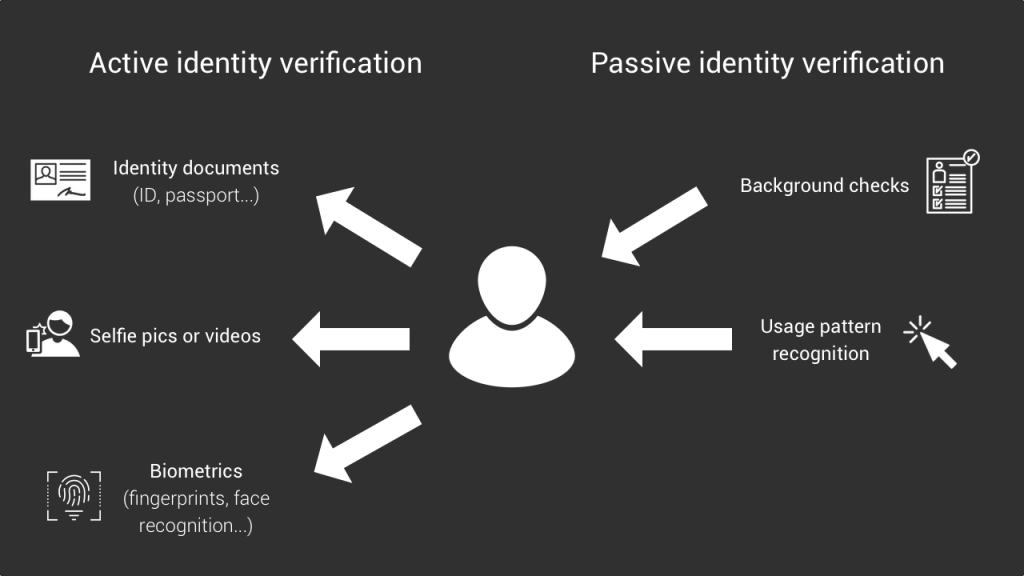
Far from all services ask you to actively confirm your identity, but many of them will do it in the background, without you knowing it. For example, simply based on an email address or a credit card number they can run quite a long list of verifications thanks to identification databases.
Sometimes this verification even happens based on product usage, without any personal information as an input. For instance, some social media platforms are not allowed to let children under 13 years old to create an account. And in order to catch the ones who lie about their age during the signup, they have put in place pattern recognition algorithms based on product usage that detect when users are potentially younger than what they declared. As you can see id verification is not only about confirming a particular identity but also to detect specific demographics (Are you above 13yo?).
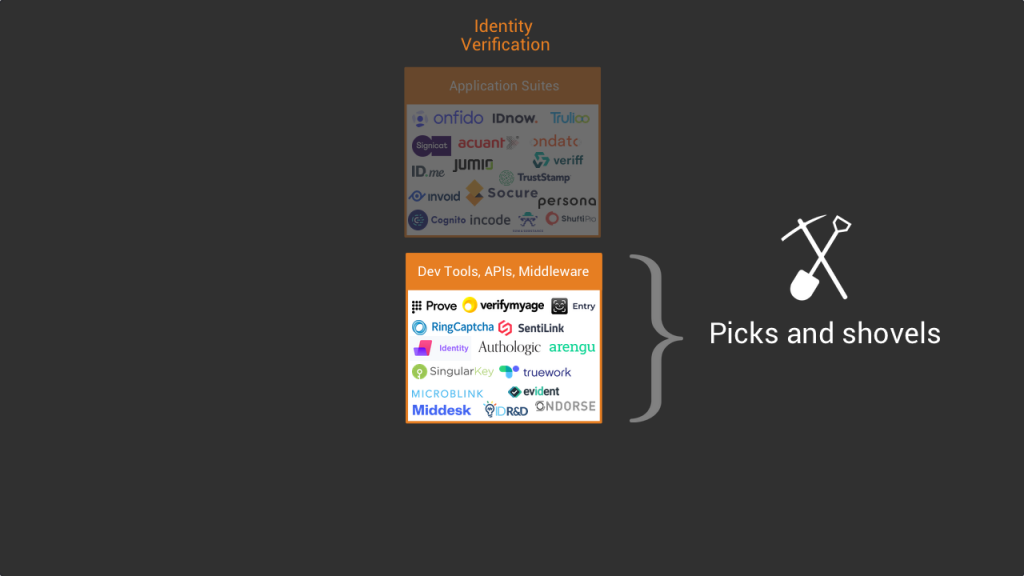
In the infrastructure and middleware layer you’ll find the services that enable developers to create their own id verification process and orchestration services.
As we saw, there’s a growing number of ways to confirm the identity of users. As a consequence there’s an increasing number of “pick and shovel” startups that provide the technology to do that. For example IDRND is a technology company specialized in biometric authentication with facial and voice recognition, or microblink for documents. But you also have in this group “databases” companies that provide for example publicly available criminal records.
Since the id verification stack is increasingly fragmented there’s a growing need for orchestration services that enables businesses to connect the different verification services they use and consolidate id verification across different channels or products.
Tech Trends
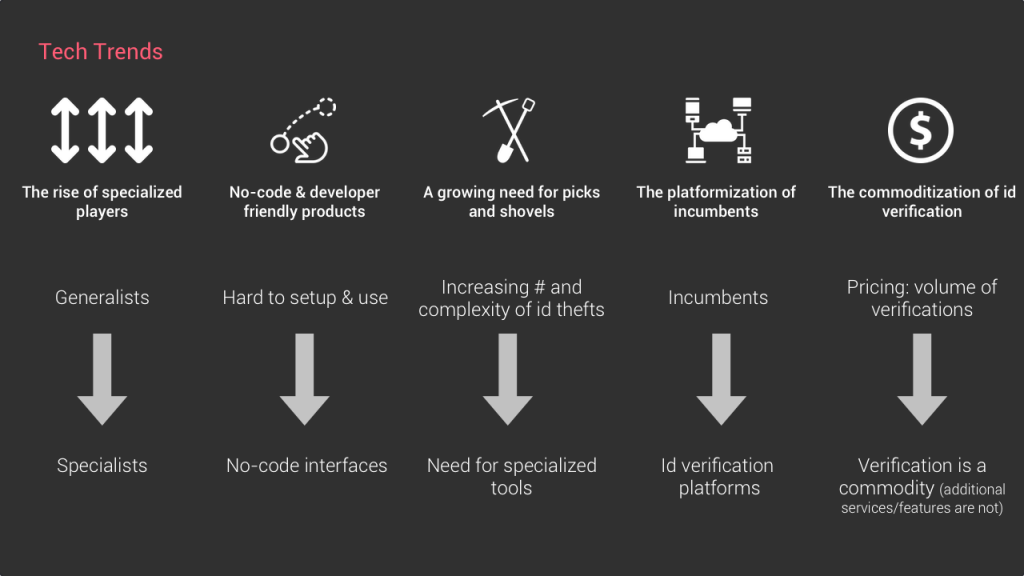
#1 The rise of specialized id verification players
The explosion of use cases for id verification is creating a need for more flexible products and personalised experience. A marketplace in the gig economy might not have the exact same needs compared to a company in the finance space or a mobile gaming editor. To answer these needs, we see a growing trend of specialized players emerging in the space. This specialization can be a focus on specific industries, use cases or even in some geographics as legal requirements can be quite different from one country to the other.
The big question is whether in a space already dominated by huge players such as Onfido or IDNow there is still space for more large companies or if these new players will stay “niche”. My personal belief is that there’s such an explosion in terms of need that the market is getting far larger than before and as a consequence these verticlized id verification providers can become huge companies. I might be wrong, but it’s my opinion at the moment, the market is definitely getting deeper.
#2 no-code and developer friendly products
Another consequence of the broadening of the identity verification market is that the products in that space must appeal to a broader audience. Historically, since most id verification providers were selling their tool to large companies in the financial industry, the products were often “enterprise” type of products meaning that they needed a lot of resources to set up and use.
What we see currently emerging is a new breed of products which are targeting developers directly and with a much more modern approach based on simplicity and ease of use. You don’t need a team of ten engineers and months of installation before you can use these new products. The sales motion is expanding to a more bottom up approach where developers can test themselves a solution before committing to it. In that perspective we saw an increasing number of low code and no code id verification products that provide both flexibility and personalization.
#3 A new breed of pick and shovel
In the middleware layer what stood also out is the rise of pick and shovel products. As we explained, the race between hackers and businesses is an ever ending one with hackers coming with more and more sophisticated attacks to steal and fake identities. This is why we constantly need new ways to verify the identity of users and this task becomes increasingly complex from a technical point of vue. As a consequence a growing number of startups focus on providing this technology only and offer “pick and shovels” to the identity verification industry.
#4 The unbundling of incumbent
Coming back to the application layer and the explosion of use cases, one of the challenges for the incumbents is to stay relevant. The customers and use cases are so diverse that the major players cannot keep up with this demand in terms of product and they risk being unbundled by the smaller but more specialized newcomers.
To answer this challenge, many of them know that they won’t be able to compete on the pure product aspect, so the big question is how they can become platforms and become the identity hub where their customers will consume other id products. Think of how Salesforce transitioned from a pure CRM to now a real platform for businesses. This is why orchestration is becoming key as the identity verification stack is becoming increasingly fragmented,
#5 The commoditization of id verification
The last trend I’ll cover is about the business model and the commoditization of identity verification. The pricing structure of most incumbents is quite complex but a key element in that space is that a big chunk of the pricing relies on the volume of verification you process. The more you verify the identity of users the more you pay.
But since there’s more and more players providing these services, there’s a growing competition around pricing and newcomers are super aggressive with the way they price their service.
This race toward the commoditization of id verification has many impacts whether it’s in terms of pricing, unit economics and even the extra features which are monetized.
4- Web 3 Auth and Self-Sovereign Identity
Issues with the current verification and authentication models
So far the user authentication and identity verifications solutions we covered are based on two models:
- The centralized identity model
- And the Federated identity model
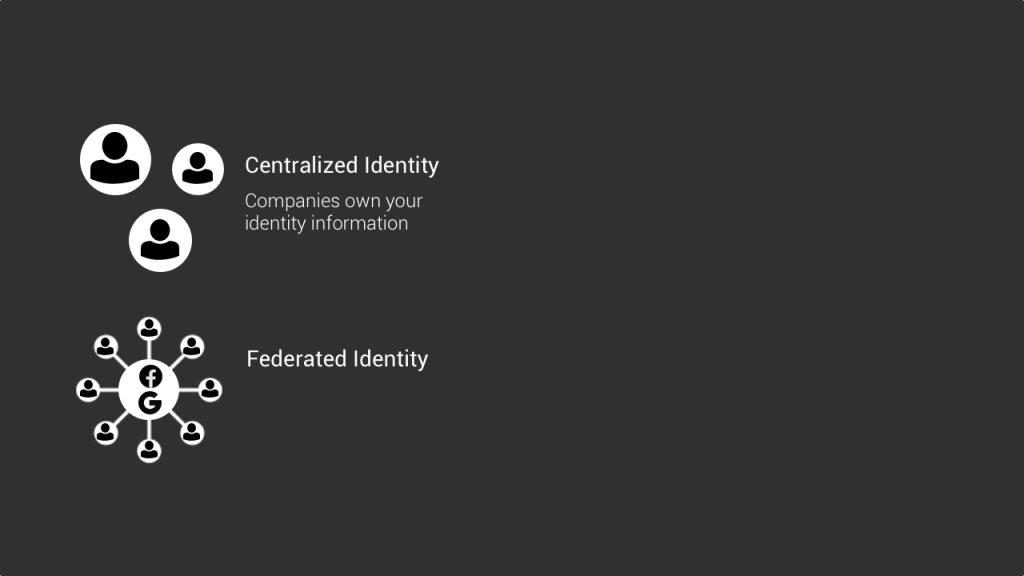
The centralized identity model is when a service provider requires you to create an account, for example with your email and a password, and controls this account and the information linked to it. From your name, to your password, your credit card information or other types of info.
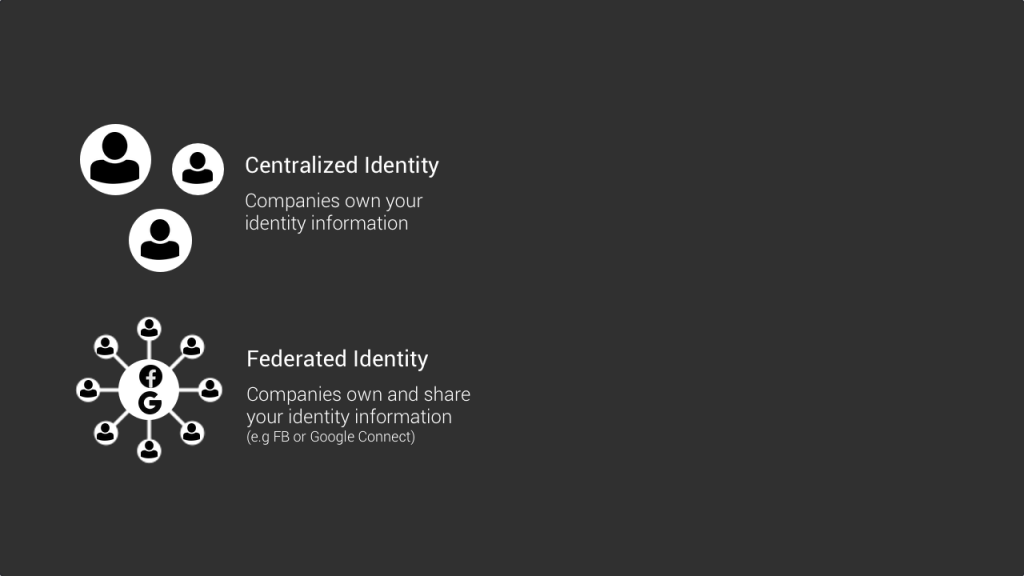
The federated identity model is when a single account can be used to login to different services. Think of your Facebook account that you can use to register to other services thanks to the Facebook connect button.
While these two models are the most widely used, three problems are inherent to them.
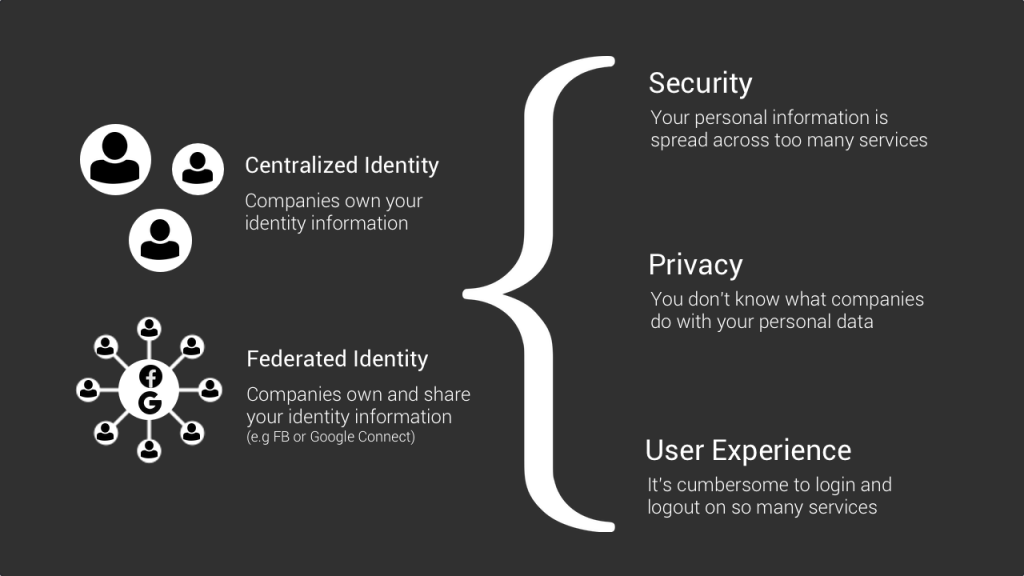
The first problem is about security and the fact that with the centralized model, plenty of different companies store sensitive information about you and if they get hacked, you can be in a lot of trouble if it’s a password that you use across other services or if it’s your credit card number. The more your identity related information is stored in different places you don’t control, the more chances they’ll get hacked.
The second problem is linked to privacy. Whether it’s with federated or centralized identity, the service providers own your data. And very often these service providers will use your data for other reasons from marketing, to targeted ads or just to improve their product. The problem is that you rarely have your word to say about it, so in terms of privacy it’s really not in favour of the users.
The last problem is about user experience. As we saw in the video about authentication services, an email is linked, on average, to 150 online accounts. And obviously it’s a pain to have to login and logout everywhere. This UX issue is partly solved by the federated identity model that precisely enables you to connect to different services with the same account, but having a central and unique online identity where you login to whatever services you want while being the owner of your information would be much more convenient.
And it’s precisely the promise of a new identity model which has accelerated the past couple of years: Web3 auth.
The promise of Web3 auth: Self-Sovereign Identity
The aim of this part is not to go deep into crypto and blockchain territories but rather to provide a broad overview of what is happening in terms of identity management and how it could potentially play out with the different blocks we described in the previous videos.
First of all, when I speak about Web3, I speak about the decentralized web built on top of crypto and blockchain tech. One of the many promises of web 3 is to enable users to manage and control their identity themselves rather than by third parties such as Facebook or Google.
Unlike centralized and federated identity, web 3 auth is based on what is called self-sovereign identity which works through the combination of three parties:
- The identity owner
- The credential issuer
- And the credential verifier

The identity owner is the user. Basically you and me. Our identity is a set of different clusters of information coming from different providers. For example your national government is the one that issues your national id card containing your name, date of birth and nationality. Another cluster of personal information about you can be your financial status. And in this case, the entity handling it might be your bank. Another cluster of info is about your education with all the diplomas and certifications delivered by the schools and universities that you attended.
In the self-sovereign model, these clusters of information are called credentials and the entity delivering them are the credential issuers.
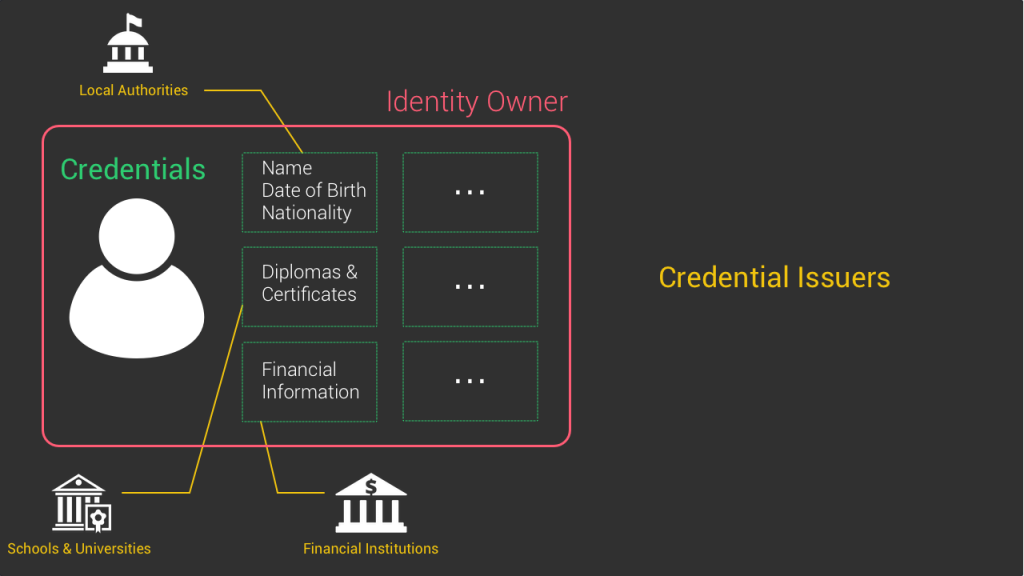
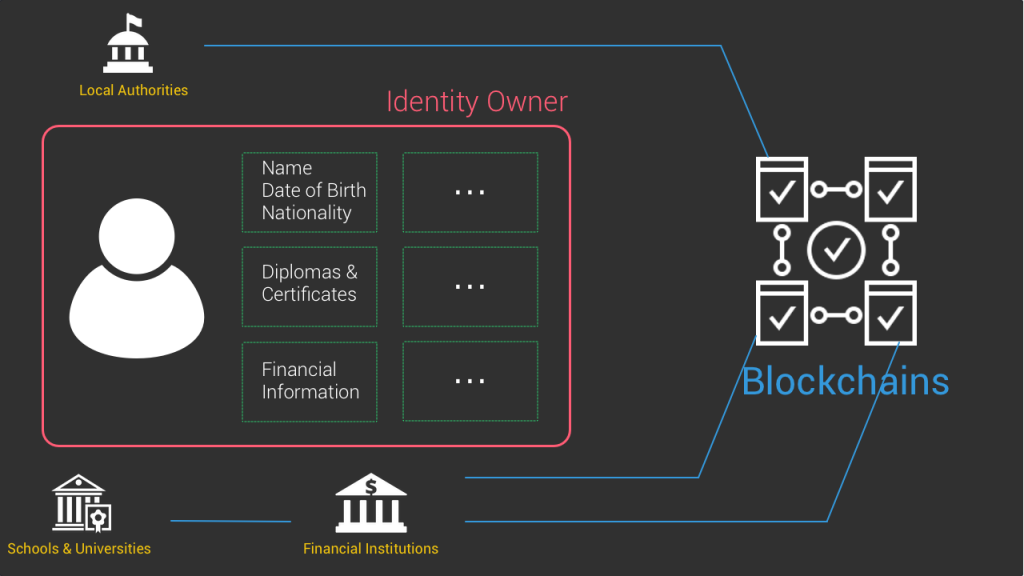
Now you’ll probably ask me where the innovation is because so far it doesn’t sound like anything new under the sun. Well, in our case it’s the use of cryptography and blockchains tech to orchestrate how these different elements interact together.
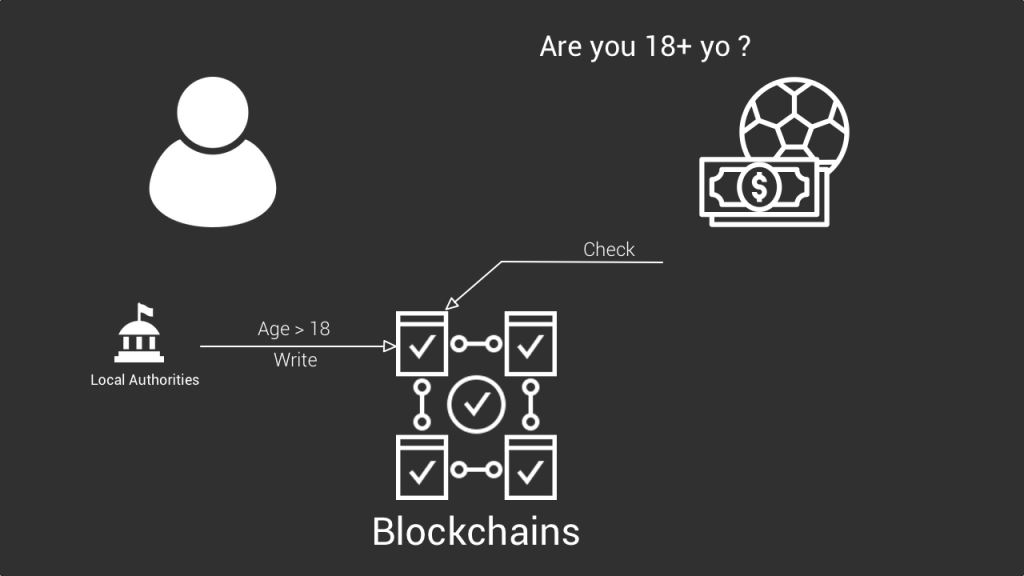
Without diving into too much details. As the identity owner you own the information defining your identity . What the issuers are doing is to write proofs about your credentials on blockchains that anyone can check when you claim something. They don’t write personal information, but just certifications of certain claims. A bit like stamps of approval.
For example, let’s say that in order to register for an online betting service, I need to prove that I’m older than 18 years old. With the traditional model I need to upload a picture of my id card directly to this betting app. Which can be dangerous.
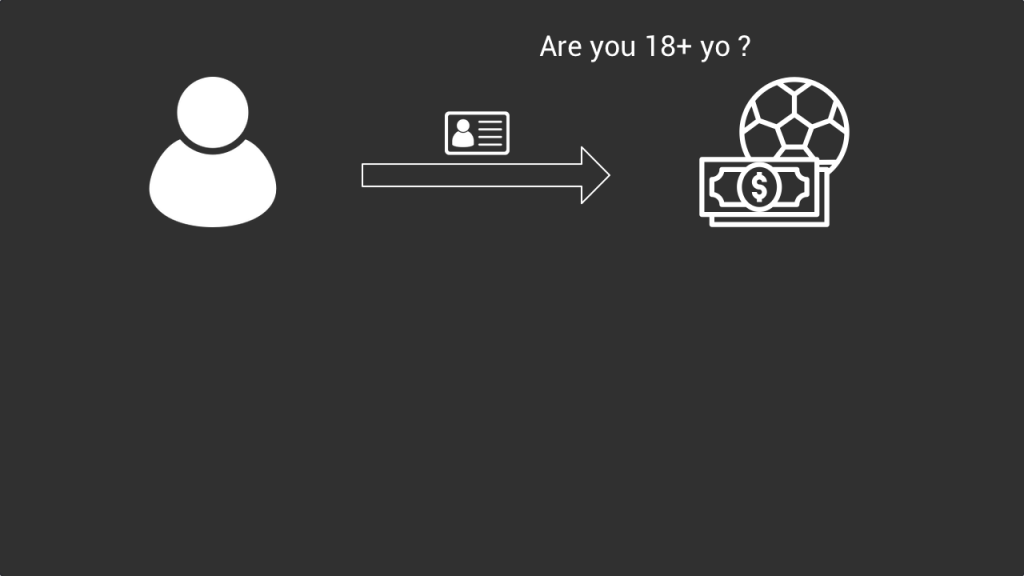
With the self sovereign identity model I don’t need to send them a scan of my id card, they will just check on the blockchain if my claim of being over 18 years was validated by the government who wrote a proof on a blockchain. If it’s the case they will just let me use their app without them accessing my date of birth or my address and the other sensitive information displayed on my id card.
The advantages are manifold:
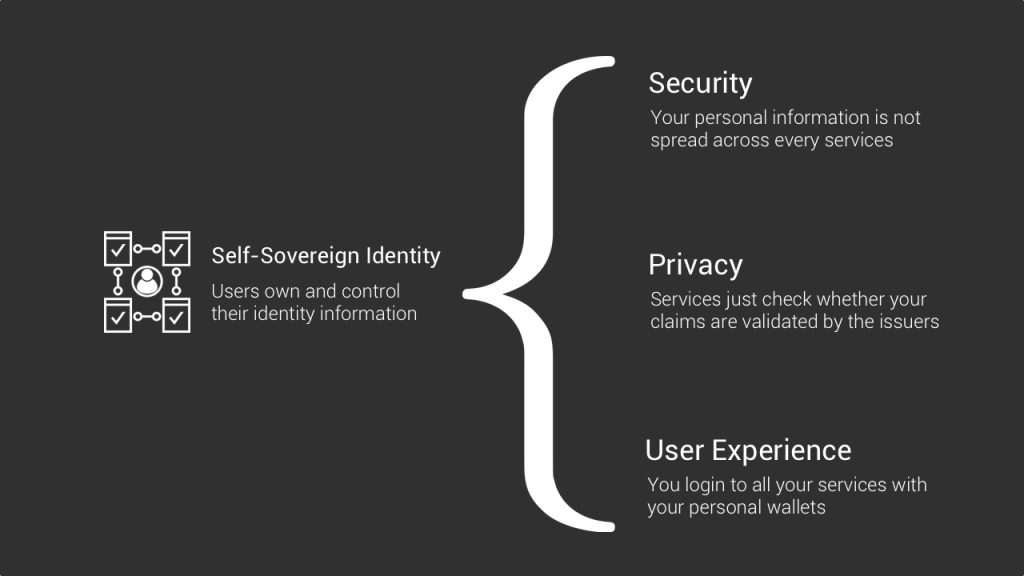
- First I don’t spread my personal information around, and as a consequence there’s less risk that it gets stolen somewhere else.
- Second, the credential verifier, in our case the betting service I want to subscribe to, doesn’t even need to contact the government to get a proof. They just check the official stamps that were written on a blockchain.
- Third, as a user I can register to many services without creating new accounts. I just use my personal wallets to login and logout to the various services I want to use.
Of course all of this is also subject to debate and plenty of people say that this self-sovereign identity is not a silver bullet and still have security and privacy flaws. But I’m not here to debate that and the point is not to say that one model is better than the other but rather to say that traditionally centralized and federated identity were the two most used models, but a third models is emerging, self-sovereign identity, and that in the years to come it will probably impact the broader online identity management space that we’re exploring in these videos.
Tech Trends
#1 the emergence of web 3 auth auth/id stack
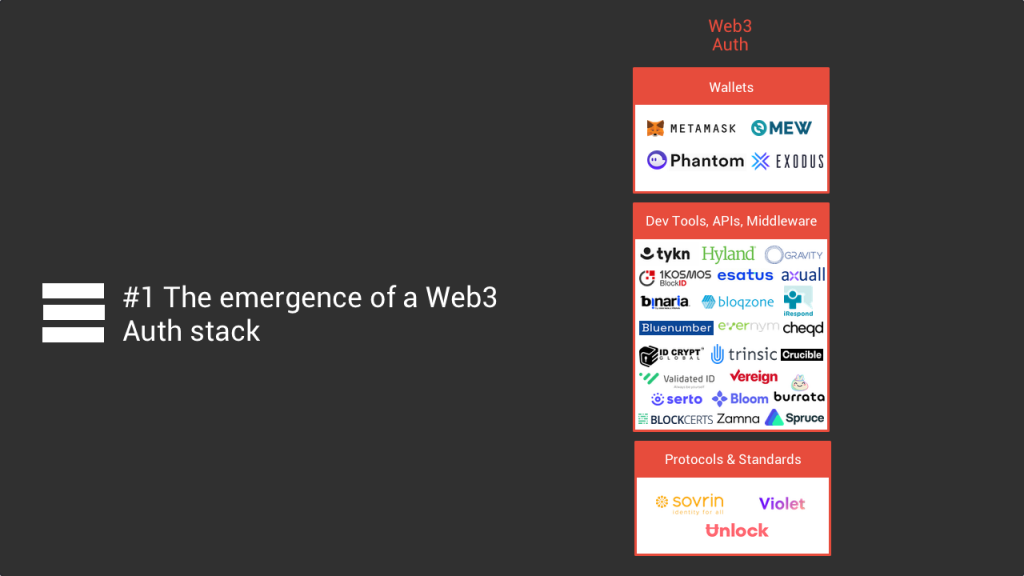
The first trend that we see in the current environment, is the emergence of an identity stack similar to what we saw with authentication and id verification, but based on crypto and blockchain tech. We also divided this stack into three layers with wallet applications on top, followed by middleware and finally the identity protocols at the bottom.
#2 Crypto wallets are the gate to managing user auth/identity
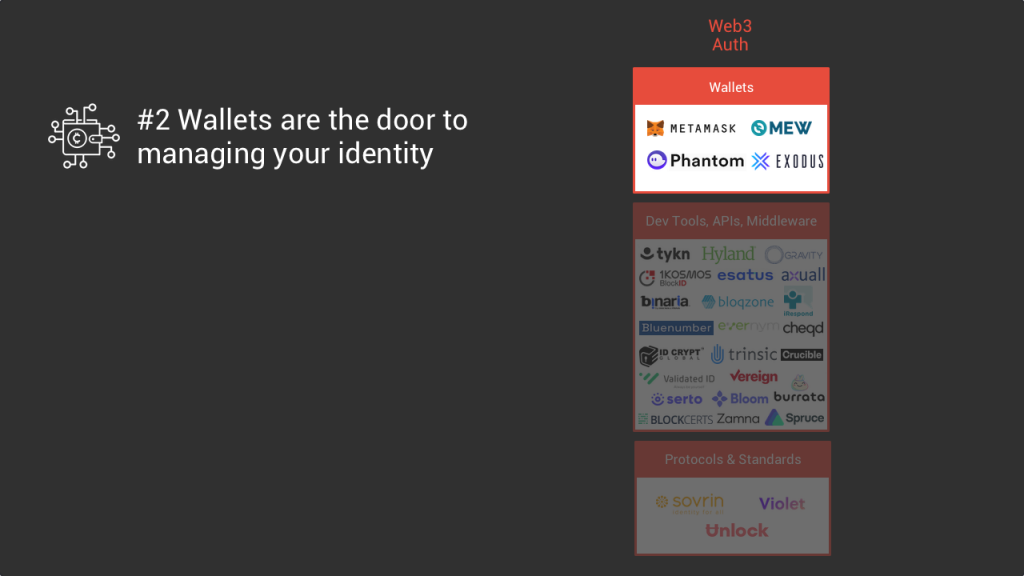
Since the user is the owner of his identity information in the self-sovereign identity model we decided to put at the top of the stack the wallet applications that enable people to store their credentials and access keys. These are the central products through which people will login and identify themselves to access apps and services. Metamask and Phantom are good examples of wallet pure players, but plenty of other services can provide their own wallets where you can store the credentials specific to certain services.
#3 A need for web 3 auth developer tools
In the API/Developer tools layer you’ll find the tools that businesses can use in order to manage all the operations around wallet and credential issuance and verification. For instance if you’re a business and that you want to provide to your users web3 auth functionalities without having to code everything from scratch, you can use products such as Tykn which has an API to create wallets as well as to issue and verify credentials easily.
#4 Specialized protocols are emerging

In the “protocol” layer you’ll find the blockchain protocols that these developer tools use, whether they are specialised such as sovrin which is an open source, decentralized, public identity network metasystem to create, manage, & control self-sovereign digital identity” or general purpose ones such as Ethereum. Or unlock protocol which is a PAM for the blockchain era.
Just as a side note, identity products built on top of blockchain tech are not new. A first generation of them were launched a couple of years ago but the majority of them have shut down because they never found traction. What we see now is a more structured and mature tech stack emerging, and a big question is whether this time real adoption will follow.
#5 The crossover of web3 auth to any online products.

At the moment, the majority of services that implement web3 auth are blockchain native applications a.k.a Dapp. Currently with your Metamask wallet you are mostly able to access NFT or crypto services. You cannot yet login to your Facebook or Slack account with a crypto wallet, but the current narrative in the industry is that this line will blur and one day you’ll be able to connect to any services with your email, a.k.a centralized identity, with a gmail or facebook connect, aka federated identity, and soon with a crypto wallet as a third option . Rather than being limited to Dapps only, web3 auth will be available on any type of service. That being said, we’re still early there and it’s still unknown whether this crossover will really happen and how fast the adoption will be.
Conclusion
In conclusion, our aim was not to go deep into how self-sovereign identity works nor to provide an exhaustive overview of the players in this space. Our aim is to share the big picture of what is happening in the broader online identity space. And for sure Web 3 auth is a trend that you cannot avoid and that you will likely hear more about in the years to come.
If we link this web 3 auth block to our previous auth and id verification blocks, what I believe is that:
- First, we’re still early in the adoption of web 3 auth solution and I think that it will take a bit of time before you can login to your Salesforce account with a wallet based product.
- Second, personally I’m not a crypto maximalist so I don’t believe that web 3 auth will kill and replace all other authentication solutions. I’m more in the camp of those who think that self-sovereign identity will be used alongside side centralized and federated identity.
- Third, I’m really curious to see whether traditional players such as Okta or Onfido will offer wallet based solutions at one point or if it’s only pure web 3 auth players who will win.
List of the companies on the map
If you want your company to be added on the map: clement.vouillon@gmail.com
Authentication / Authorization
Application suites
- Forgerock “Digital identity for consumers and workforce”
- Fusionauth “FusionAuth is a complete identity and access management tool that saves your team time and resources”
- Ermetic. “dentity-First Cloud Infrastructure Security”
- Idemeum “idemeum gives you tools to make your workplace passwordless”
- Jumpcloud “Cloud Directory Platform AD & SSO Reimagined.”
- Okta “Okta is one trusted platform to secure every identity, from customers to your workforce.”
- Onelogin “OneLogin is the leader in identity and access management, enabling organizations to access the world.”
- PingIdentity “Identity security for the digital enterprise”
- ReachFive “Identity & Access Management Designed for the Modern Customer Experience”
- Secureauth “SecureAuth is an identity access management security solution that provides passwordless authentication”
- Trusona “Authenticate people. Not passwords.”
APIs/Developer tools/Middleware/Orchestration
- Aerobase “Open source IAM”
- Auth0 “Rapidly integrate authentication and authorization for web, mobile, and legacy applications”
- Beyondidentity “Beyond Identity is the world’s most advanced passwordless identity platform”
- Cerbos “Do not reinvent user permissions”
- Incognia “Zero-Factor Authentication. Eliminate Account Takeovers and Friction on Mobile”
- Keyri “Passwordless authentication”
- Magic “Fast, secure passwordless login for your app or website. One SDK for email magic links and social login”
- Ory “Open source identity solutions for everyone”
- Strata “Strata provides an identity orchestration platform built specifically for hybrid and multi-cloud environments”
- Stytch “User infrastructure + passwordless authentication”
- SuperTokens “Add simple email and password sign up functionality to your site or app”
- Warrant “APIs for authorization and access control”
Protocols
- OAuth 2
- Openid
- LDAP
- SAML
Identity Verification
Application suites
- Acuant “Acuant Trusted Identity Platform is a leading global provider for Identity Verification”
- Cognito “Cognito identity verification provides instant KYC and AML compliance, watchlist screening, and more”
- Checkr “Employee background check for companies”
- Digital Identity “Verify and sign-up your customers in seconds through their bank app and OneID”
- ID.me “Simple secure identity verification”
- IDnow “The identity verification platform. Built for security. Loved by users. “
- inVoid “Instant customer onboarding KYC”
- Incode “Incode offers the most advanced identity verification and authentication platform”
- Jumio “Jumio’s identity verification, eKYC and AML solutions fight fraud and other financial crimes”
- Ondato “Ondato provides solutions for identity verification, data monitoring, screening, due-diligence, risk screening”
- Onfido “Onfido is building the new identity standard for the internet. We let your users verify their identity”
- Persona “Online ID verification service to help any business, from any industry, collect, verify, and manage user identity”
- Shufti “Verify users through Digital KYC Services, and perform background checks in under 60 seconds”
- Signicat “One point of integration for all your digital identity needs across borders”
- Socure “Accurately verify & onboard more new customers with Socure”
- Sumsub “KYC/AML & Identity Verification Service”
- Synaps “Synaps verify your users in the easiest way possible. Simply integrate our solution to your website and get ready to begin.”
- Trulioo “ the leading global identity verification service”
- Truststamp “Secure, Private & Trusted Identity”
- Veriff “Complete Identity Verification and KYC platform. Know that people are who they say they are“
APIs/Developer tools/Middleware/Orchestration
- Arengu “Arengu is a low-code platform that allows you to build sign-up or authentication flows”
- Authologic “Create custom scenarios using one or many verification methods. Standalone or in sequence.”
- Entry “Biometric identity provider”
- Evident “End-to-end automated insurance verification”
- IDRD “ID R&D offers biometric authentication security technologies for enterprise customers”
- Microblink “Solution for scanning of identity cards, payment slips, invoices, receipts”
- Middesk “Business verification and risk assessment”
- Prove “The modern way of proving identity with just a phone.“
- RingCaptcha “Onboard & engage users in 90s with phone identity, verification, OTP & SMS notification”
- Sentilink “identity verification”
- Singular key “No-code identity orchestration”
- Stripe Identity “Stripe Identity lets you programmatically confirm the identity of global users”
- Truework “Employment and income verification”
- Verifymyage “VerifyMyAge provides a seamless age verification online solution for any online product.”
Web 3 Auth / Self-Sovereign Identity
Developer tools
- 1Kosmos “ BlockID is the world’s only cybersecurity solution that combines indisputable digital identity proofing with advanced biometrics and passwordless authentication for your workforce and customers.”
- Axuall “The Axuall platform automatically aggregates and verifies credentials that can be shared between clinicians and organizations in realtime.”
- Binaria “Identity Validation on demand within a practical and safe ecosystem”
- Bloom “Unlock DeFi’s Full Potential with Reusable, Verifiable Credentials”
- Blockcert “Build apps that issue and verify blockchain-based credentials”
- Bloqzone “Identify your customer before you say hello”
- Bluenumber “Our mission is to change how people own, manage, and benefit from use of their digital identity and data”
- Burrata “Bridging web2 to web3”
- Cheqd “The authentic data network. We enable new business models for verifiable credentials“
- Ceramic “IDX, Ceramic’s identity system, supports DIDs for cross-chain IDs, streams for storage, and hubs for linking streams to a user”
- Crucible “Tools for builders & creators, portable digital identity for players.”
- Esastus “Start using modern SSI technology and give users complete control back over their own identity”
- Evernym “The world’s leading platform for verifiable credentials”
- Gravity “Digital identities for financial inclusion”
- Hyland “Get a complete system to issue digital credentials in a blockchain-secured format that is easily shareable and instantly verifiable anywhere in the world.”
- IDCript “ID Crypt Global provides a global cloud native platform for true digital identity and identity related services”
- Irespond “Privacy-Protecting Biometric Identity Solutions”
- Spruce “Self-Sovereign Identity. SpruceID is an ecosystem of open source tools to enable user-controlled identity anywhere.”
- Trinsic “The proof of anything platform“
- Tykn “Your login box. Powered by the blockchain.”
- Validated “Provide trust to your electronic signatures and digital identity”
- Vereign “Email as a better alternative to traditional registered mail. Your first step to Self Sovereign identity”
- Zanma “Unlock the power of verifying traveller health and identity data pre airport and pre departure”
Protocols
- Sovrin “Sovrin has three networks for self-sovereign identity.”
- Violet “A new identity protocol built on Ethereum”
- Unlock protocol “Unlock is an open source, Ethereum-based protocol designed to streamline membership benefits for online communities.”
Startups unpacking
Persona: Continuous Identity Verification
🏬 Company
Pitch: @persona_idv is a customer identity infrastructure platform that enables businesses to build their personalized identity verification (KYC) processes.
Category: #IdentityManagement – #KYC
🩺Pain Point
As our lives happen more and more online, businesses increasingly need to verify who their users are and conduct “KYC” (Know Your Customers).
Verifying users’ identity is a complex process that you cannot do by yourself and which is often mandatory (regulation).
👫Value props & Persona
Persona is a suite of tools that enables businesses:
- Verify the identity of their users (API as a service)
- Build their own identity verification workflows (software)
Developers are the end users and risk/security management the decision makers.
💡Differentiation
Most KYC platforms offer identity verification only during signup. Persona differentiates by providing an infrastructure for “continuous ID verification” to continuously check whether users are really who they say they are throughout a product lifecycle.
💵 F(o)unding
The company was founded in 2018 by former Square and Dropbox engineers and has raised a total of $220M with the latest round being a Series C of $150M in September 2021.
(This software category is very capital intensive).
👷♂️⛏ To dig further
On the vision of the identity verification space: https://withpersona.com/blog/series-c
Magic Link: Passwordless authentication
🏬 Company
Pitch: @magic_labs is a developer tool that provides a SDK to easily implement passwordless authentication in your app.
Category: #IdentityManagement – #DeveloperTools
Pain Point
Most apps need to build an authentication system to enable users to signup & login to their product = must-have problem.
Most of them are based on passwords (not secure), but the trend is toward passwordless auth: 1 time links & passwords or biometric.
👫Value props & Persona
Magic enables developers to easily integrate passwordless auth to their product.
The company is mostly used by crypto companies, but they want to expand their audience and target any type of businesses.
💡Differentiation
1️⃣ Unlike many auth providers which are enterprise products, Magic adopts a bottom-up approach by targeting developer first (product lead growth with a freemium).
2️⃣ Under the hood their tech is based on decentralized identity and leverage blockchain tech.
💵 F(o)unding
The company was launched in 2018 by former Docker, Uber and Yelp engineers.
It appears that they really started to get traction in 2020/2021 and recently raised a $27M Series A.
Links to go further
Website: https://magic.link
Blog: https://medium.com/magiclabs
PH: https://www.producthunt.com/posts/magic-11
TC: https://techcrunch.com/2021/07/22/magic-27m-series-a-for-its-plug-and-play-passwordless-tech/